Deepfake scams target corporates: New study warns of rising AI-powered fraud
Unlike traditional phishing, deepfake-driven social engineering leverages hyper-realistic audio or video to increase the credibility of fraudulent requests. The study provides examples where scammers impersonated a CEO’s voice to steal $243,000 and, in another case, used synthetic video to convince a finance employee to transfer $25 million during a fake executive conference call.
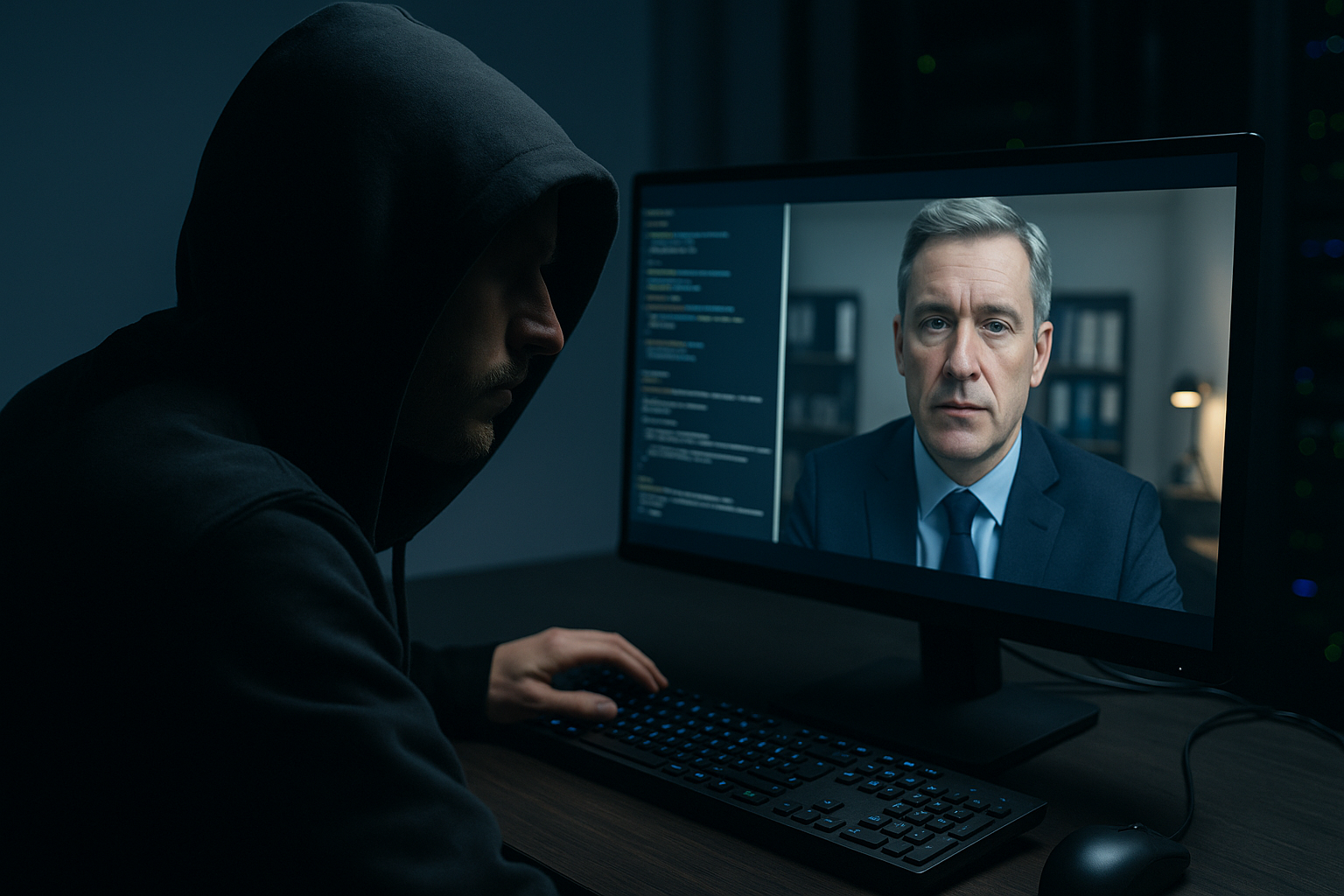
Deepfake technology, once confined to social media satire and political misinformation, is now weaponized in corporate settings, powering a new generation of social engineering attacks that exploit trust, bypass security, and inflict real financial damage. A groundbreaking study titled “Deepfake-Driven Social Engineering: Threats, Detection Techniques, and Defensive Strategies in Corporate Environments”, published in the Journal of Cybersecurity and Privacy, brings this threat into sharp focus. Conducted by researchers at the Technical University of Denmark (DTU), the study presents one of the most comprehensive assessments to date on how organizations are grappling with this rapidly evolving cybersecurity challenge.
Drawing on expert interviews with cybersecurity professionals from major firms in Europe and integrating a robust review of current detection methods and attack case studies, the authors reveal a sobering reality: while awareness of deepfake threats is growing, most corporations remain ill-equipped to detect or defend against these sophisticated impersonation schemes. As incidents involving AI-generated fake voices and videos of executives requesting wire transfers or sensitive data continue to rise, the report issues a clear call to action - adapt security frameworks now, or risk operational and reputational fallout.
How are deepfakes weaponized in corporate attacks?
The report defines deepfakes as synthetic media, video, audio, or text, generated through machine learning techniques, particularly generative adversarial networks (GANs). In the context of corporate attacks, these technologies are used to impersonate executives, hijack trusted communication channels, and manipulate employees into taking unauthorized actions such as transferring funds or sharing confidential data.
Unlike traditional phishing, deepfake-driven social engineering leverages hyper-realistic audio or video to increase the credibility of fraudulent requests. The study provides examples where scammers impersonated a CEO’s voice to steal $243,000 and, in another case, used synthetic video to convince a finance employee to transfer $25 million during a fake executive conference call.
What makes these attacks particularly dangerous is their capacity to bypass traditional cybersecurity tools. Antivirus software, spam filters, and even multi-factor authentication offer little protection against an employee who is visually and audibly tricked into believing they are interacting with a real, high-level superior. Moreover, with the increasing availability of easy-to-use deepfake generation tools, the barrier to executing such attacks is rapidly lowering.
What are the gaps in current detection and defense measures?
Despite the urgency, the study found that none of the interviewed organizations had implemented dedicated deepfake detection tools. Instead, companies rely on general cybersecurity frameworks provided by vendors like Microsoft, which are not specifically tailored to identifying AI-generated forgeries.
Detection remains a major challenge. While some organizations have begun experimenting with AI-based classifiers like convolutional neural networks (CNNs) and forensic metadata analysis, these efforts are nascent, fragmented, and often face barriers related to scalability and integration into existing workflows. Moreover, false positives can erode trust in detection systems, while the lack of real-time processing limits their utility during live interactions such as video calls or instant messaging.
Training also falls short. Most employees are briefed on phishing or malware threats, but few receive specific education on identifying deepfake content. This leaves a gaping vulnerability, especially given that studies cited in the report show that 27–50% of individuals cannot distinguish between real and deepfaked video footage.
One of the most notable contributions of the study is the introduction of the PREDICT framework - a comprehensive defense lifecycle encompassing Policies, Readiness, Education, Detection, Incident Response, Continuous Improvement, and Testing. It’s a call for corporations to move beyond reactive measures and adopt a proactive, structured approach that integrates policy reform, technical upgrades, and human-centered awareness programs.
What can companies do to prepare for deepfake threats?
To mitigate the growing risk of deepfake-driven fraud and manipulation, the study offers several actionable recommendations rooted in its interviews and technical assessments:
-
Invest in Dedicated Detection Tools: Companies must integrate machine-learning models trained on deepfake datasets into their security stack. This includes classifiers for real-time video and audio stream analysis, as well as metadata cross-checking tools for asynchronous media.
-
Update Employee Training Programs: Security awareness training should include practical exposure to deepfake examples and simulations. This is especially critical for high-risk roles such as finance, legal, and public communications.
-
Revise Incident Response Protocols: Current playbooks must be updated to include specific steps for suspected deepfake incidents - such as isolating content, triggering multi-channel verification, and notifying stakeholders quickly.
-
Adopt Zero Trust Frameworks: The report endorses a Zero Trust model with continuous verification, least-privilege access, and advanced authentication methods (e.g., biometric or behavioral analysis) to mitigate the damage from identity forgery.
-
Forge External Partnerships: Collaboration with cybersecurity vendors, law enforcement, and AI research institutions is critical to staying ahead of emerging deepfake capabilities and building shared defense intelligence.
-
Monitor Legal and Regulatory Changes: Companies should align their internal policies with emerging data protection and AI disclosure laws such as the GDPR and EU’s AI Act, which are increasingly focused on traceability and accountability in synthetic content creation.
Looking ahead, the study urges companies not to view deepfakes as a distant or niche concern. While some firms have yet to experience direct deepfake attacks, the trajectory of generative AI tools suggests that this threat will only intensify - growing more affordable, more convincing, and more accessible to malicious actors. In such a climate, failing to plan is planning to fail.
- READ MORE ON:
- deepfake corporate threats
- AI impersonation attacks
- deepfake cybersecurity
- social engineering with deepfakes
- deepfake detection tools
- AI-driven phishing
- how deepfakes are used in corporate impersonation fraud
- deepfake detection for enterprise cybersecurity
- best practices for deepfake attack prevention in business
- FIRST PUBLISHED IN:
- Devdiscourse










